Cybersecurity is a significant aspect for individuals and organizations as society has become more reliant on technology. Computer systems are being used every day and each user has a responsibility to secure their computer and data. Therefore, cybersecurity plays an important role in preserving computing systems and information.

The Three Essential Concepts of Cybersecurity
- Confidentiality: restricted or private information must remain the same and it can be obtainable for allowed users only (“Tech Computer Science”, 2020).
- Integrity: in order for information to maintain its ethics, it must not be modified from its existing condition (“Tech Computer Science”, 2020).
- Availability: information that is accessible for valid users to access whenever they want (“Tech Computer Science”, 2020).
The Importance of Cybersecurity
Cybersecurity provides various benefits to businesses and corporations nowadays. Firstly, it secures the organization’s possessions such as all the information that is retained in the computer networks. Secondly, it follows the rules and requirements of the government as well as ethical obligations. Every organization creates regulations and policies in response to the security requirements. These regulations are crucial for companies that utilize computer and they provide security to the companies. Furthermore, companies could gain a competitive advantage over another as network security appears to be the main component in attracting customers to use the online and financial services (“Tech Computer Science”, 2020). Consequently, it helps to control and limit the large numbers of cybersecurity threats such as phishing, vishing, smashing, and whaling (“Tech Computer Science”, 2020).
The Different Types of Cybersecurity Threats
- Phishing is the act of sending scamming emails which resembles financial institution (CISCO, n.d.). The purpose is to steal the private information from the recipients such as account numbers passwords, and usernames.
- Ransomware is a type of malicious software, which intended to get money from the victim by blocking access to the computer system unless the victim pays the ransom (CISCO, n.d.). However, it cannot be guaranteed that the system will be fully restored even though the ransom has already been paid.
- Malware is a type of software that harms the users in a variety of forms such as controlling or gaining access to the user’s computer without authorization, encrypting and altering the user’s private information (CISCO, n.d.).Social Engineering is an act of deceiving the victim to expose their confidential data such as banking information and passcodes.
- Social engineering can go together with the above threats which allow more users to access links and download malware (CISCO, n.d.).
What is the Impact of Cybercrime on Businesses?
Having insufficient cybersecurity could result in many consequences:
- Losing corporate information and computing system causes businesses to suffer from economic costs as they have to pay for restoring and repairing the systems.
- Losing customer trusts due to lack of security which largely affects the company’s reputation and profits.
- Suffering from regulatory penalties because the General Data Protection Regulation violates the rules (Tunggal, 2020).
Successful Cybersecurity Approaches
Businesses and organizations can be protected against complex cyber-attacks by ensuring adequate cybersecurity practices.
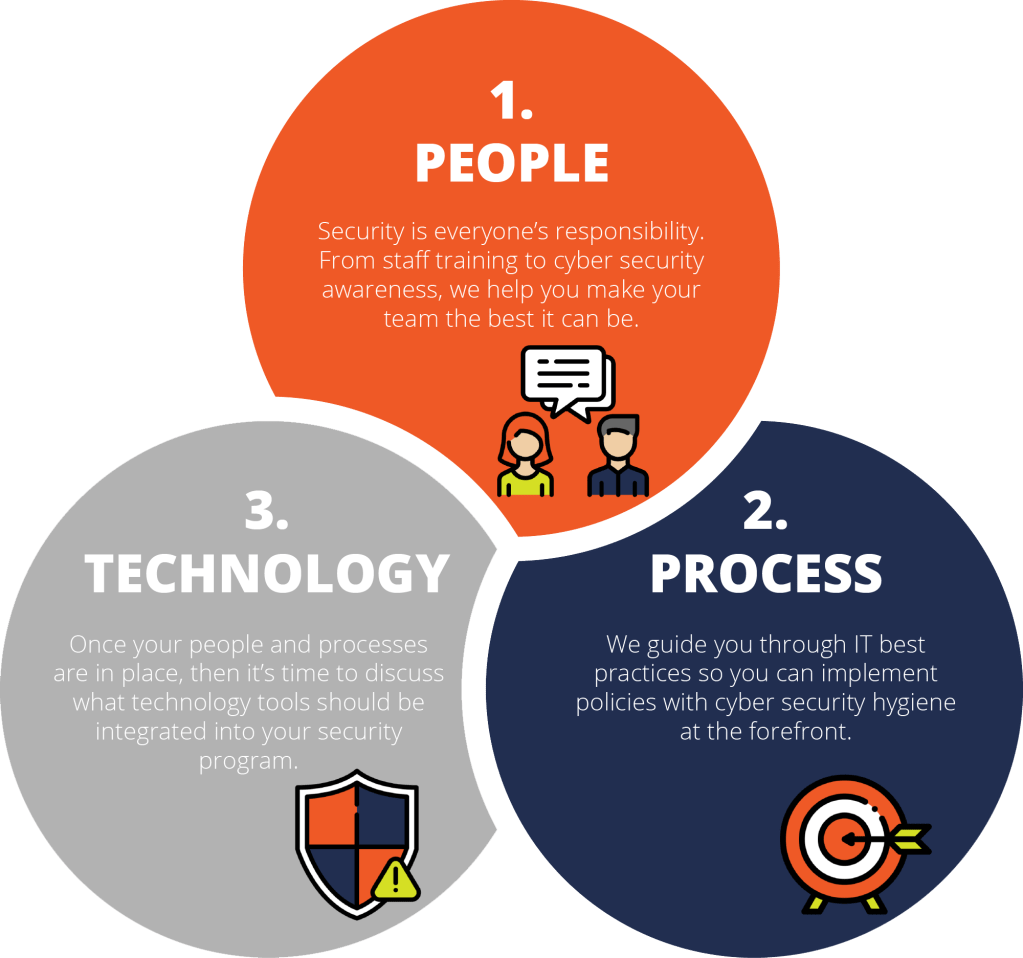
- One of the uppermost steps is to increase security through informing and teaching every individual in the corporation to acknowledge the consequences of cybercrime. Moreover, they should understand more about the basics of cybersecurity concepts and the dangers of social engineering. For instance, the primary ways of securing the data are generating strong or difficult passwords and being cautious with unfamiliar email attachments (Tunggal, 2020).
- Another step is to have an outline of how organizations handle cyber-attacks. This outline helps to explain and determine the types of cyber-attacks, how to secure the computer systems, how to discover and react to the damages, and how to regain back from the attacks (CISCO, n.d.).
- Apart from that, computer security tools are also vital in getting rid of cyber-attacks. The mainstream types of technologies that are used to protect routers, networks, devices and the cloud from the attacks are firewalls, antivirus software, malware protection, and DNS filtering (CISCO, n.d.).
References
CISCO. (n.d.). What Is Cybersecurity?. Retrieved from https://www.cisco.com/c/en/us/products/security/what-is-cybersecurity.html
Tech Computer Science (2020). Computer Security. Retrieved from https://teachcomputerscience.com/computer-security/
Tunggal, A.T. (2020). Why is Cybersecurity Important?. Retrieved from https://www.upguard.com/blog/cybersecurity-important